In today’s interconnected world, ensuring the safety and security of our digital devices is more crucial than ever. Recently, a concerning incident revealed how hackers managed to deliver malware to Windows and Mac users by compromising an Internet service provider (ISP) and tampering with software updates. This blog post will break down the technical aspects of this attack in a way that’s easy to understand.
The Incident: An Overview
Researchers from Volexity, a cybersecurity firm, discovered that hackers had infiltrated an ISP’s network infrastructure to redirect software update requests to malicious servers. This attack affected various applications, including 5KPlayer, Quick Heal, Rainmeter, Partition Wizard, and software from Corel and Sogou.
How the Attack Worked
1. ISP Compromise
The hackers gained control over the routers or similar network devices of an unnamed ISP. By compromising these devices, they could manipulate the network traffic passing through them.
2. DNS Poisoning
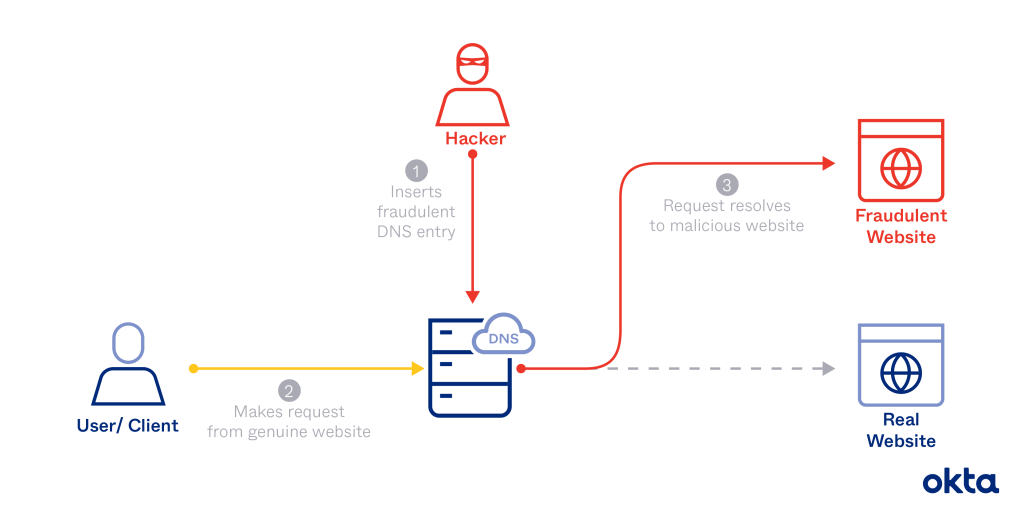
DNS, or Domain Name System, is like the internet’s phone book, translating human-friendly domain names (like www.example.com) into IP addresses that computers use to identify each other on the network. In this attack, the hackers used a technique called DNS poisoning to alter the DNS responses.
Normally, when your computer requests the IP address for a website (like an update server), it trusts the response it gets from a DNS server. The hackers manipulated these responses, redirecting update requests to malicious servers instead of the legitimate ones.
3. Insecure Update Mechanisms
The affected applications used unencrypted HTTP (Hypertext Transfer Protocol) connections or lacked cryptographic signatures to verify the authenticity of the updates. This lack of security allowed the hackers to perform man-in-the-middle (MitM) attacks, intercepting and altering the data being transferred.
4. Delivery of Malware
For example, the 5KPlayer app checked for updates using an insecure HTTP connection. The hackers redirected this request to a malicious server that provided a harmful configuration file. This file then downloaded a further payload disguised as a PNG (Portable Network Graphics) image, which was actually executable malware. On macOS, this malware was known as MACMA, and on Windows, it was called POCOSTICK.
The Malware: MACMA and POCOSTICK
MACMA: Initially identified by Google in 2021, this malware targets macOS (Apple’s operating system for Mac computers) and iOS (Apple’s operating system for mobile devices) devices, offering capabilities like device fingerprinting, screen capture, file downloading and uploading, executing terminal commands, audio recording, and keylogging.
POCOSTICK (MGBot): In use since at least 2014, this Windows malware is known for its versatility and has been used by a Chinese-speaking group known as Evasive Panda. It can be installed through legitimate software updates that have been tampered with.
Preventive Measures
1. Use Secure Update Mechanisms
Ensure that software updates use encrypted connections (HTTPS, which stands for Hypertext Transfer Protocol Secure) and cryptographic signatures to verify the authenticity of the updates. This prevents unauthorized modifications during transmission.
2. Employ DNS Over HTTPS or TLS
To protect against DNS poisoning, use DNS over HTTPS (DoH) or DNS over TLS (Transport Layer Security). These protocols encrypt DNS queries, ensuring they can’t be intercepted and altered by attackers. Popular DNS services like Google (8.8.8.8) and Cloudflare (1.1.1.1) offer these secure options.
3. Stay Informed and Vigilant
Keep informed about the latest security threats and practices. Regularly update your software and operating systems to the latest versions, which often include important security patches.
Conclusion
This recent attack highlights the importance of secure software update mechanisms and robust network infrastructure. By understanding how such attacks work and implementing preventive measures, we can better protect our digital devices and personal information from malicious actors.
Stay safe online, and always be cautious of the software you download and the sources you trust for updates.
Credit: This post is based on information from a detailed report by Dan Goodin on Ars Technica. You can read the full original article here.